How to deactivate your phone for 5 minutes can protect you from hackers
Technological experts say that this form of "cyberhygience" can protect your data.

If you have already called technical support on your computer or phone, you are very familiar with the first question that is asked: have you tried to deactivate it and go? Maybe you rolled your eyes to this suggestion after treating Current problems , but a restart East Often a quick and reliable solution. And deactivate your device can have other important advantages. Experts advise that restarting your phone is not only useful for small fixes, but can also protect you from hackers. Read the rest to find out how to deactivate your phone for only five minutes can help ensure the safety of your device.
Read this then: Never charge your Android phone when it is 0%, say the experts .
Consider restarting your phone every day.

Keeping your phone out of pirates sometimes looks like a difficult battle. We are constantly reminded of updating our software and regularly changing our passwords. But the Australian Prime Minister Anthony Albanian , explains that deactivating your phone for only five minutes is an underestimated defense line.
"We all have a responsibility. Simple things, turn off your phone every night For five minutes, "Albanese told Australian residents while appointing the country's national cybersecurity coordinator, by The Guardian . "For people who look at this, do it every 24 hours, do it while you brush your teeth or everything you do."
Albanese's advice to restart daily are more frequent than weekly restarts recommended by the National Security Agency (NSA) in its mobile device best practices Guide, published in 2020. However, experts say that there is no difficulty in restarting more regularly.
Technological experts claim that restart should be part of your routine.

This five-minute break break offers you a little protection against spy software, because it closes your active applications and stops all the processes that run in the background, Priyadarsi Nanda , PhD, lecturer at the Sydney University of Technology, said The Guardian . This is particularly important, because you may not realize that malicious applications are active on your phone. AE0FCC31AE342FD3A1346EBB1F342FCB
"If there is a process going on the contradictory side, the deactivation of the phone breaks the chain, even if it is only for the time the phone is deactivated, it certainly frustrates the potential pirate," said Nanda.
This advice seems quite simple to follow, but it could help define a daily reminder, because the restart is "a good cyberhygiene" which decreases certain risks, ARASH SHAGHAGHI , PhD, lecturer in cybersecurity at the University of New South Wales, said The Guardian .
In relation: For more information, register for our daily newsletter .
The restart makes hacking more difficult.

While Shaghaghi warns that this trick cannot protect you from each threat - as if your password has already been stolen - the disturbance can always be "a drawback".
As Neal Zero , the technical director of the NSA cybersecurity management, told the Associated Press in 2021: "It is Imposing cost On these malicious actors. ""
Disabling your phone is particularly important for attacks "zero click on a click, which do not force you to click on a listening or a summary email so that a hacker can access. According to Shaghaghi, the restart" can challenge Attackers because they may need to find alternative ways to exploit the device when mounted. "
There are other key tips to ensure safe.
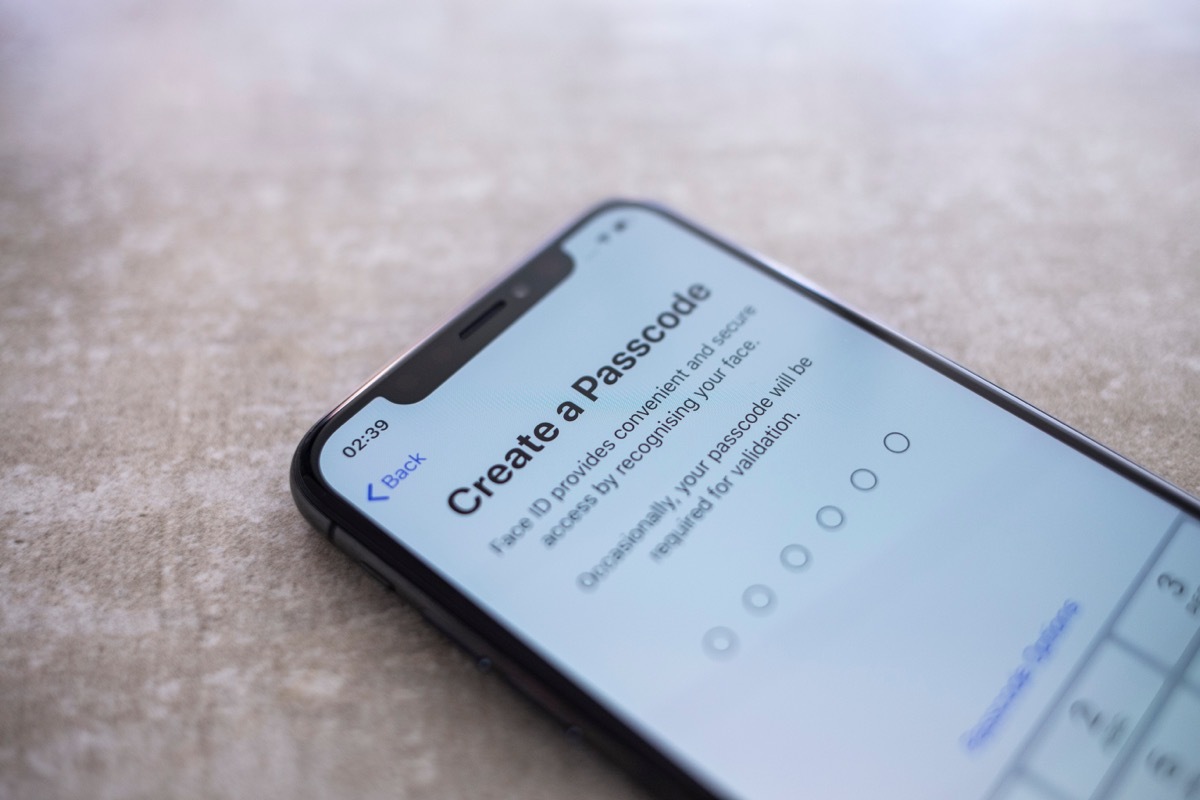
In addition to a daily or weekly restart, the Federal Trade Commission (FTC) also has some tips to protect your phone from pirates. The agency always recommends keeping your phone locked with a six -digit access code , and ensuring that you alone can access it via fingerprints, retina or facial recognition.
The FTC reiterates the need to keep the software up to date, as well as to make a backup of your phone. You must also activate a system that helps you locate your phone if you lose it - or erase all your data if it is found in bad hands.

Oliver Stone said that working with Richard Dreyfuss was "the worst experience" of his career

